Vulnerabilities in controller of refrigeration equipment
In this blogpost Stan Plasmeijer and Jony Schats will describe the vulnerabilities discovered in the AK-EM100 controller. This blogpost won’t include a proof of concept of the atttacks since there are still devices connected to the internet and the vulnerabilities discussed are of high risk. The AK-EM100 is a physical device and provides a web based graphical user interface of a store which allows a range of daily users to monitor data, alarms and reports, either locally or remotely, regarding all of their refrigeration equipment.
Together with DIVD we have disclosed the following five vulnerabilities:
- CVE-2023 – 22583 SQL Injection
- CVE-2023 – 22584 Cleartext credentials
- CVE-2023 – 22585 Reflected Cross-Site Scripting
- CVE-2023 – 22586 Local File Inclusion
- CVE-2023 – 25911 OS Command Injection
Below is a brief description of each CVE and our recommendation.
CVE-2023 – 22583 SQL Injection
The login form of the device is vulnerable to a union based SQL injection. With this SQL injection it’s possible to retrieve information from the database, which will be returned in the location header of the response. By injecting a single quote a SQL error is shown:
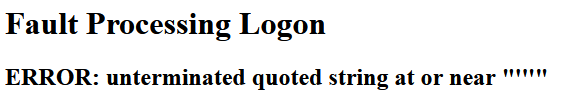
CVE-2023 – 22584 Cleartext credentials
The database saves login information in cleartext (readable format). This means that the passwords of the users aren’t hashed. Hashing turns a users password into a short string of letters and/or numbers using an encryption algorithm, hashing passwords is a best practice.
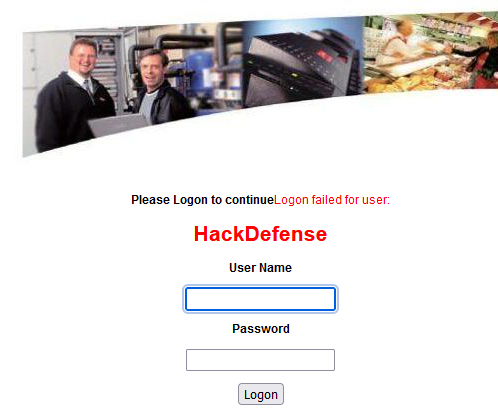
CVE-2023 – 22585 Unauthenticated Reflected Cross-Site Scripting
The login form of the AK-EM 100 reflects the username value when the login is invalid. It doesn’t sanitize the input, so if you input HTML or JavaScript it reflects this directly into the webpage. In the screenshot below we injected <h1>HackDefense</h1> into the username field.
CVE-2023 – 22586 Local File Inclusion
The file parameters in the configuration pages are vulnerable for a Local File Inclusion vulnerability. This can be used to read system files.
CVE-2023 – 25911 OS Command Injection
Once authenticated it is possible to execute operating system commands from a webpage and take over the device. Once the device is taken over it is possible to pivot into the internal network the device is connected too. Due too the sensitivity of this vulnerability we won’t disclose specifics.
Recommendation
Our recommendation is to disconnect the AK-EM 100 from the internet or only allow specific IP-addresses to access the device. Danfoss their recommendation is to phase out the AK-EM 100.
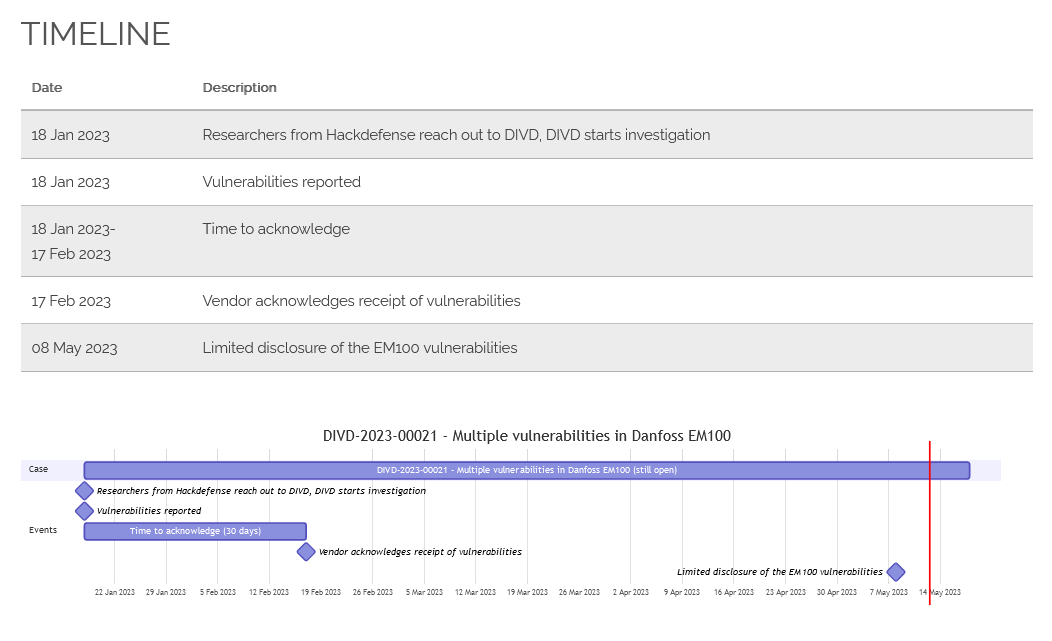
Timeline of the DIVD case