The importance of SMB signing
When testing Windows environment, we regularly see the encrypted password of a user with high privileges being sent accros the network. In combination with systems where SMB signing is disabled, an attacker or malicious person can, by performing an NTLM relay attack, increase the privileges within the network. Depending on the network environment an attacker may be able to increase privileges to the highest level.
Windows maakt gebruik van veel verschillende authenticatieprotocollen. Eén van die protocollen is Net-NTLM. Dit protocol authenticeert gebruikers over het netwerk. Er bestaan twee versies: Net-NTLMv1 en Net-NTLMv2. Beide versies berekenen een zogeheten Net-NTLM-hash door het versleutelde wachtwoord van een gebruiker te verwerken in een willekeurige string bestaande uit acht bytes. Net-NTLMv1 is vanzelfsprekend minder veilig dan Net-NTLMv2 en wordt sinds Windows Vista en Windows Server 2008 standaard uitgeschakeld.
Windows uses many different protocols for authentication. One of those protocol is Net-NTLM. This protocol authenticates users over the network. There are two versions: Net-NTLMv1 and Net-NTLMv2. Both versions compute a so-called Net-NTLM hash by processing a user’s encrypted password into a random string consisting of eight bytes. Net-NTLMv1 is obviously less secure than Net-NTLMv2 and has been disabled by default since Windows Vista and Windows Server 2008.
The image below shows that, using responder, the user’s Net-NTLM hash was obtained hackdefense.
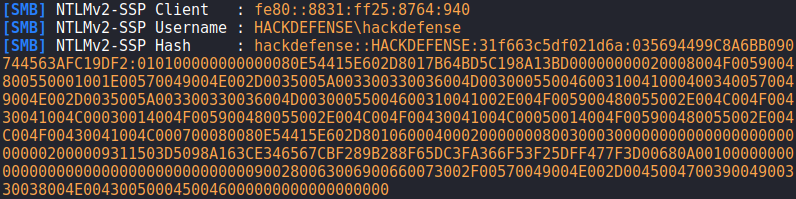
An attacker can try to do two things with this hash:
- Crack it with John the Ripper or Hashcat. However, the success rate depends on the strength of the password. A strong password will not be cracked easily.
- With this hash, an attacker can also perform an “NTLM Relay Attack”.
NTLM Relay Attack
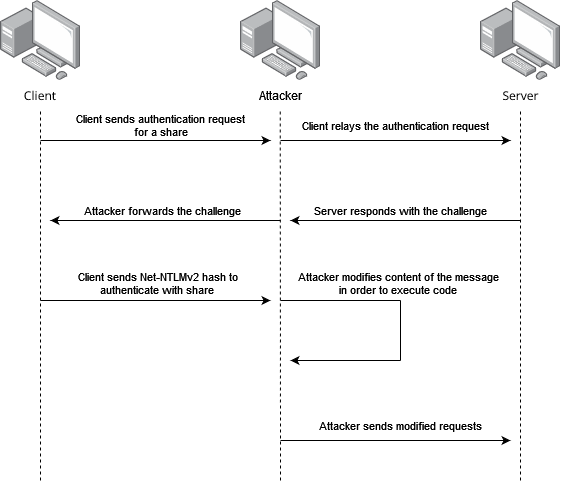
An NTLM relay attack exploits the Net-NTLM protocol. An attacker intercepts a legitimate authentication request and forwards it to a computer. This authenticates the attacker on the target system in the context of the user who sent the request. This would allow the attacker to access network drives that he or she should not have access to or execute arbitrary code on the underlying system. The image below shows the operation of an NTLM relay attack on a high level.
crackmapexec smb 192.168.126.0/24 --gen-relay-list targets.txtThis checks the address range 192.168.126.0/24 for machines on which SMB is open and SMB signing is disabled. The IP addresses that match are written to the ‘targets.txt’ file. Next, we use of the tools Responder and ntlmrelayx utilities. Responder is responsible for capturing the Net-NTLM hash and forwards it to ntlmrelayx, which then authenticates itself on the specified host(s) via SMB with the hash it has received. To accomplish this, the SMB and HTTP server must be disabled in Responder’s configuration. This can be done by opening the configuration file and changing the values behind SMB and HTTP to ‘Off’. The configuration file should look like this:

Next, Responder must be started on the active network interface, in this case eth0. This can be done by running the following command: responder -I eth0 -r -d -w.
Finally, we use the ntlmrelayx utility to extract the contents of the SAM database from the target systems. To do this, we start ntlmrelayx with the following command:python3 ntlmrelayx.py -tf targets.txt. Once ntlmrelayx receives a Net-NTLM hash from Responder, ntlmrelayx tries to authenticate to the systems in the targets.txt file. If authentication is successful, ntlmrelayx then attempts to extract the contents of the SAM database. To do this, the user whose hash has been captured must have local administration rights on the target system. In addition to extracting the SAM database, it is also possible to execute other system commands.
The image below shows a successful NTLM relay, where the user had local administration rights on the target system and thus the contents of the SAM database could be extracted.
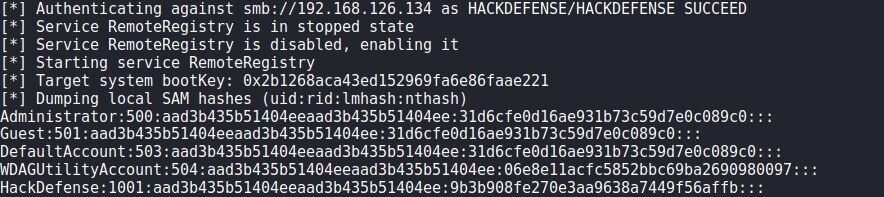
An attacker would now be in possession of the encrypted password of the local administrator. This gives an attacker local administration rights on this system. This allows the attacker to extract the encrypted passwords of users, who have or recently had a session, from memory. In the event that this includes a domain administrator, an attacker can increase the privileges to Domain Admin and thus take over the entire domain.
We regularly observe that the password for the local Administrator user is reused on multiple computers. This means that an attacker can use the same password to log on to multiple computers as a local administrator. This broadens the attack vector and increases the likelihood that the attacker can increase his or her privileges.
Recommendation: SMB Signing
Systems are susceptible to an NTLM relay attack because the recipient does not verify the content and origin of the message. The most effective way to remedy this vulnerability is to enable enterprise-wide SMB signing.
SMB signing is a security mechanism in the SMB protocol. When SMB signing is enabled, each SMB message is sent with a signature in the SMB header field. The signature consists of the contents of the SMB message, encrypted with the AES algorithm. This allows the recipient of the SMB message to verify that the content of the message has been changed. It also verifies the identity of the sender. If the content of the message doesn’t match the SMB header, the recipient knows that the message has been tampered with. The recipient then does nothing with this SMB message. This makes it impossible to successfully perform an NTLM relay attack.
SMB signing can be enabled by setting the contents of the EnableSecuritySignature and EnableSecuritySignature registry values to 1. This must be applied to both the LanManServer and the LanManWorkstation. This can be done in two ways: via a system command or via the graphical application ‘Local Group Policy Editor’ (gpedit.msc).
SMB signing can be enabled via the command line by running the following commands:
reg addHKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanManWorkstation\Parameters\/v EnableSecuritySignature /t REG_DWORD /d 1reg addHKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanManWorkstation\Parameters\/v RequireSecuritySignature /t REG_DWORD /d 1reg addHKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanManServer\Parameters\/v EnableSecuritySignature /t REG_DWORD /d 1reg addHKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\LanManServer\Parameters\/v RequireSecuritySignature /t REG_DWORD /d 1
This will overwrite the current contents of the registry value. Afterwards the system needs to be restarted.
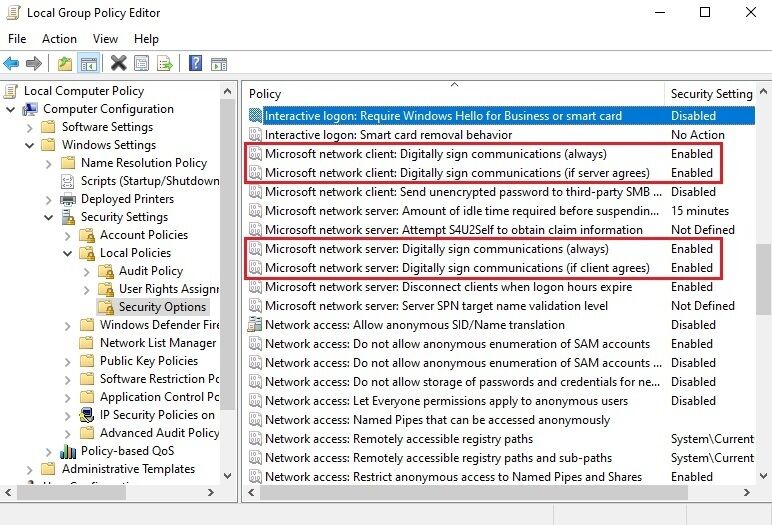
From the graphical application ‘Local Group Policy Editor’, SMB signing can also be enabled. In the application, navigate to Computer > Windows Settings > Local Policies > Security Options. Then change the value of the policies below to Enabled. After this the system needs to be restarted.
- Microsoft network client: Digitally sign communication (always)
- Microsoft network client: Digitally sign communication (if server agrees)
- Microsoft network server: Digitally sign communication (always)
- Microsoft network server: Digitally sign communication (if client agrees)
On Linux, SMB signing can be enabled by opening the configuration file for Samba and adding the lines below under global settings. After this the SMB service needs to be restarted.
client signing = mandatoryserver signing = mandatory
